MoniMaster Support: Monitor devices with others' permission.
Today's digital environment demands computer monitoring as an indispensable means of protecting individual privacy and online productivity. From parents, employers, or individuals looking for ways to safeguard personal information - computer monitoring provides us with an invaluable way of maintaining safety and productivity online.
However, a critical question often arises: how to monitor another computer screen without them knowing? Our journey delves into the nuanced world of monitor personal computer practices, showing how technology offers the cloak of invisibility and the lens of oversight, ensuring a balance between security and discreet observation.

Can I See Someone Else's Computer Screen Without Their Knowledge
Yes, there are many ways that allow you to view another person's computer screen without their knowledge. Whether it's to keep children safe online, to monitor employee productivity, or to protect sensitive information, we recommend doing so in a way that protects the privacy of others.
How to Monitor Another Computer Without Them Knowing - 3 Ways
Secretly observing another computer screen can safeguard children, increase employee performance, or protect confidential data. Demand has skyrocketed for remote monitoring software and techniques for these purposes - PCSntry monitoring solutions stand at the forefront alongside TeamViewer remote access software and even widely-used browsers such as Google Chrome; such tools offer various functions from laptop monitoring to hidden computer monitor functionality, giving complete oversight without needing physical presence from someone who oversees.
1. Use a Professional Computer Monitoring Software - PCSntry
MoniMaster PCSntry is the pinnacle of remote monitoring software, designed to operate undetectably on target computer monitors. While other monitoring tools might obtrude onto desktops or become conspicuously present within Task Manager, PCSntry maintains an invisible presence while remaining part of the digital fabric of the monitored system.
How to See Other People's Computer Screen With PCSntry Remotely
Step 1. Create an Account and Choose a Plan
Start your monitoring activities by visiting the PCSntry website and creating an account to keep your monitoring activities confidential. From there, choose an ideal subscription plan suited for you based on the features available and the device numbers being monitored.
Step 2. Install PCSntry on the Target Computer
Once subscribed, you'll receive instructions via email for installing PCSntry onto a target computer. Installation should be quick and unobtrusive with minimal interaction from target device users; once complete, PCSntry starts operating discreetly behind the scenes with no trace left behind on desktop or system processes.
Step 3. Begin Monitoring
With PCSntry installed, you can access an impressive dashboard accessible through any web browser - your command center for monitoring all activities occurring across target computers in real-time or through logs.
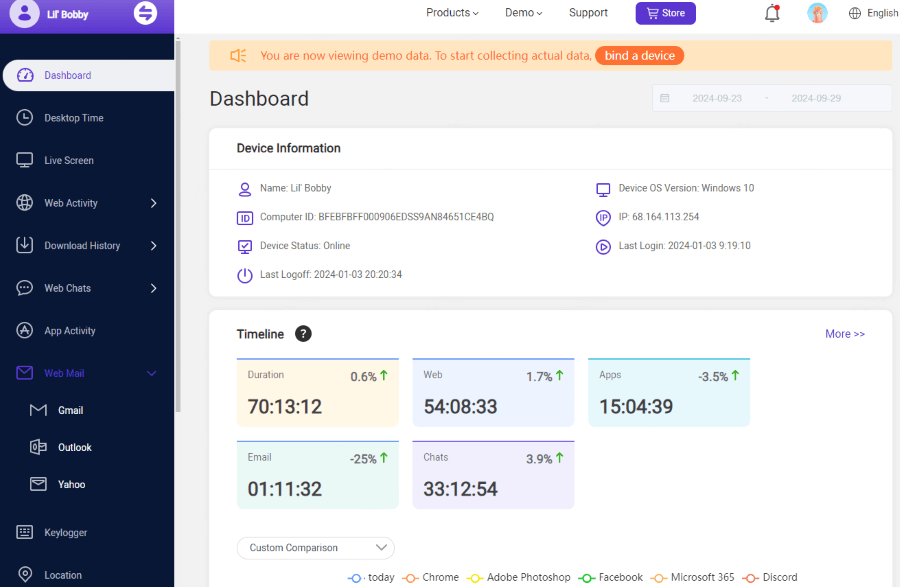
What You Can Use PCSntry to Monitor on Someone's Computer Remotely
Keystroke Logging:
Capturing every keystroke made, from passwords and search queries to sensitive ones such as sensitive passwords can give a glimpse into user intentions and activities.
Screenshots and Recording:
Acquire visual evidence of on-screen activity by taking periodic screenshots or recording for continuous sessions, making it more straightforward for individuals to understand the context and actions on screen.
Web Browsing Insights:
Monitor all web browsing activity, including visited and bookmarked pages, to gain insights into an individual user's interests and online behavior.

Email and Social Media Monitoring:
Monitor all emails and social media interactions between an account user and others to gain a comprehensive picture of their digital communications.
Application Usage:
Gain insight into which applications and programs are being utilized on an ongoing basis to assess productivity or detect unauthorized usage, providing invaluable data that enables effective decision-making or helps uncover unwarranted misuse.
Watch for files being moved, edited, or deleted to protect against data breaches or unintended access to sensitive information.
Employing PCSntry as a laptop monitoring solution or hidden computer monitor provides peace of mind and ensures digital environments - whether personal or professional - remain protected and under vigilant watch. Thanks to its comprehensive feature set and stealthy operation, PCSntry makes an ideal tool for monitoring computer activity without compromising ethics or thoroughness.
2. Use TeamViewer to See Someone Else's Computer Screen Without Knowing
TeamViewer is an iconic remote monitoring software for remote access and support; however, it also functions well as remote monitoring software. While not designed as an inherently "hidden computer monitor tool," it can provide discreet computer monitoring solutions with proper configuration.
How To Steps
Step 1. Download and Install: Both parties need to download and install TeamViewer onto their computers. The installation process is straightforward.
Step 2. Configure for Unattended Access: On the target computer, set TeamViewer for unattended access - this requires first obtaining approval from the target side.
Step 3. Connect and View: For monitoring purposes, enter the target computer's TeamViewer ID and password into TeamViewer to gain real-time screen access.
3. Monitor Another Computer Without Them Knowing by Google Chrome
Google Chrome can be leveraged as a remote desktop monitoring software through extensions that offer simple but efficient computer screen monitoring solutions.
How To Steps
Step 1. Install Chrome Remote Desktop: Both computers must have Google Chrome installed; the Chrome Remote Desktop extension must be added from the Chrome Web Store.
Step 2. Set Up Remote Access: On the target computer, follow the instructions to set up remote access - this may require initial physical access to it first.
Step 3. Access remotely: Use Chrome Remote Desktop from your computer to quickly connect with and view any target computer's screen remotely at any time.
Each method offers its own set of advantages and levels of stealth regarding computer screen monitoring. Whether you're concerned about how to tell if someone is remotely viewing your computer or seeking to monitor discreetly, it's essential to navigate the ethical and legal considerations involved. Ensuring consent and adhering to privacy laws is paramount when employing any form of digital surveillance.
FAQs About Monitor Another Computer Without Them Knowing
No. PCSntry was created explicitly for stealth computer monitoring, making it the ideal solution for those wishing to discreetly observe personal computers without drawing suspicion from target computer monitors.
Finding out whether someone is remotely accessing your computer screen monitoring can be tricky. However, any unusual mouse movements, unexpected files or programs opening, or sudden performance changes could be telltale signs that someone could remotely monitor them.
Yes, laptops can be tracked through various means, including IP tracing, Wi-Fi network history analysis, and specific tracking software. This capability is invaluable in recovering lost or stolen devices and for computer monitoring purposes to protect personal and professional data security.
Conclusion
Our exploration into laptop monitoring and hidden computer monitor techniques demonstrates the value of PCSntry as an unobtrusive, discreet monitoring solution for digital environments.
Offering unrivaled stealth monitoring capability with comprehensive monitoring capabilities, MoniMaster PCSntry stands as an unrivaled option when seeking protection for digital environments; we highly endorse it for anyone searching for undetectable computer surveillance solutions.

















