MoniMaster Support: Monitor devices with others' permission.
Can a phone be tracked without a SIM card? Cut to the chase answer is... yes! The phone is traceable if it does not have a SIM card. However, the process may require pre-measures or your phone needs to be connected to the internet or should be active.
In this guide, we'll break down clear, effective methods to track a phone without a SIM—using monitoring apps, Google and Apple tools, and even Google Maps. Plus, we'll show how to find lost SIM card without phone. Let's get started.
- Part 1: How to Track a Phone Without a SIM Card?
- 1. Use a Phone Monitoring App
- 2. Google Find My Device - For Android
- 3. My iPhone - For iPhone
- 4. Track a Cell Phone via Google Maps
- Part 2. How to Find Lost SIM Card Without Phone?
- Part 3: FAQs about Can a Phone be Tracked without a SIM Card
- Part 4: Summary
Part 1: How to Track a Phone Without a SIM Card?
Losing a SIM card without access to your phone can be stressful, but there are several ways to track or recover it. From built-in tracking tools to IMEI tracing, each method offers different advantages. Here's a comparison of the most effective options to help you track a phone without SIM or find your lost SIM card.
| Method | Setup Before Loss? | Location Data | Location Accuracy |
|---|---|---|---|
| Phone Monitoring App | ✅ Yes | SIM info, network, location logs | High |
| Built-in Tracking Service | ✅ Yes | Accurate GPS location | High (GPS-based) |
| Social Media Platform | ✅ Yes | Activity status of device | Low to None |
| Cell‑tower triangulation | ❌ No (carrier only) | Historical/precise given authority | Medium |
| Bluetooth tracker (Tile) | ✅ Yes | Short-range & crowdsourced | Low to Medium |
1Use a Phone Monitoring App
An phone GPS tracking app is a breeze to optimize mobile phone tracking. This system uses a global positioning system to determine the precise location of the device or person. Sometimes, an Android GPS tracking app can be extremely helpful in various scenarios such as tracking a family member, planning travel routes, or even recording fitness activities.
Among several excellent options, we choose MoniMaster Pro for SIM tracking of your phone remotely, and many other features.
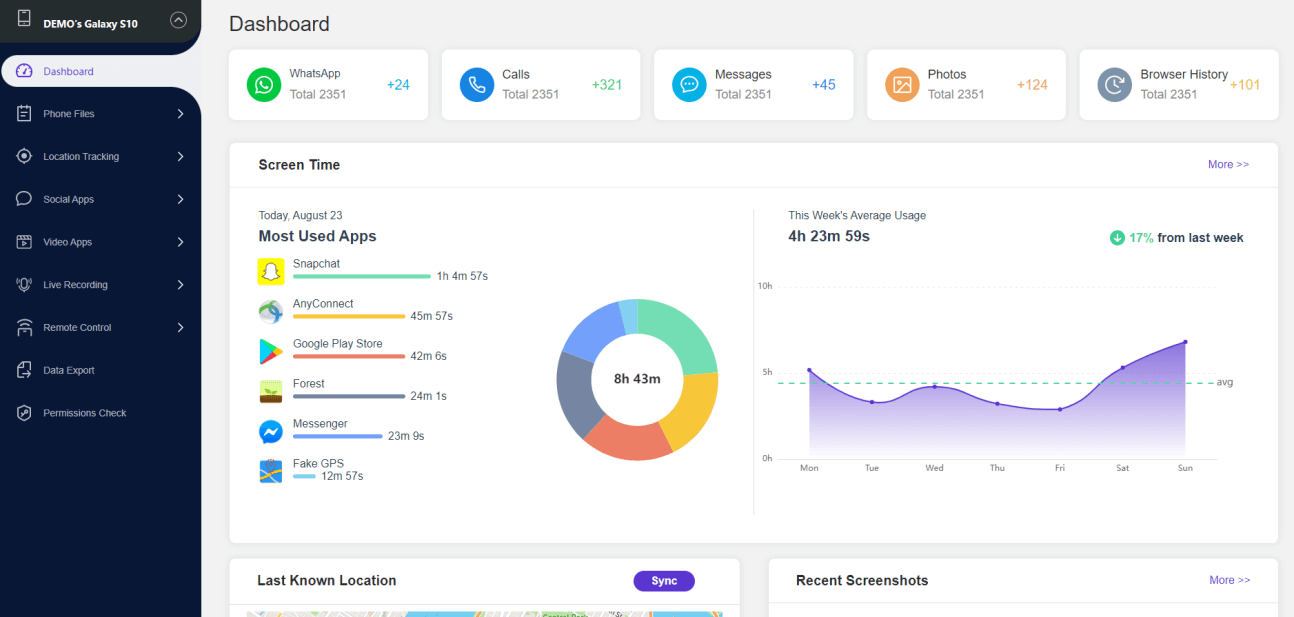
MoniMaster is an excellent facility to track location, examine files, and monitor the cellular activities of your kid. Its online data viewing dashboard ensures you have 100% secret monitoring. Accessing and examining all phone files as well as retrieving lost or deleted files to secure data.
We believe this is a safe zone for kids where you can track location or phone settings remotely. Let's dig deeper to get detailed information about the application. Track SIM card locations online for free with MoniMaster.

Key Features
There are several reasons to choose MoniMaster. Below are some prominent features:
Remote Tracking & Control: Know the current location of your family members or device without the SIM card. It provides up-to-date movements. You can track location history. Set up geofences and receive notifications. Track Wi-Fi location.
Collect Data from 30+ Apps: Check the history of over 30 popularly used apps. You can track search and viewing history on YouTube, TikTok, Facebook, WhatsApp, Snapchat, Skype, etc. The amount of time spent on videos and other activities on these applications is now handy.
Detailed insights of all phone files: Check phone loggers and text messages to know about frequent contacts. You can access contacts, call logs, photos, videos, browser history, and installed apps.
Remote stealth access with live recording: You can record audio from the surrounding environment of their device. MoniMaster facilitates real-time live recording of the screen.
Take screenshots: Taking screenshots of the target phone remotely is a breeze.
How to Find a Phone Without SIM in 3 Simple Steps
You can track your Android phone in 3 Simple Steps with MoniMaster.
Step 1. Sign Up and Purchase: Signing up is the starting point of your affiliation to the application. You need to sign up using your email address to create a valid account. Buy the plan you need.
Step 2. Download and Install: Complete the whole setup procedure. Install the app, and sign into the account.
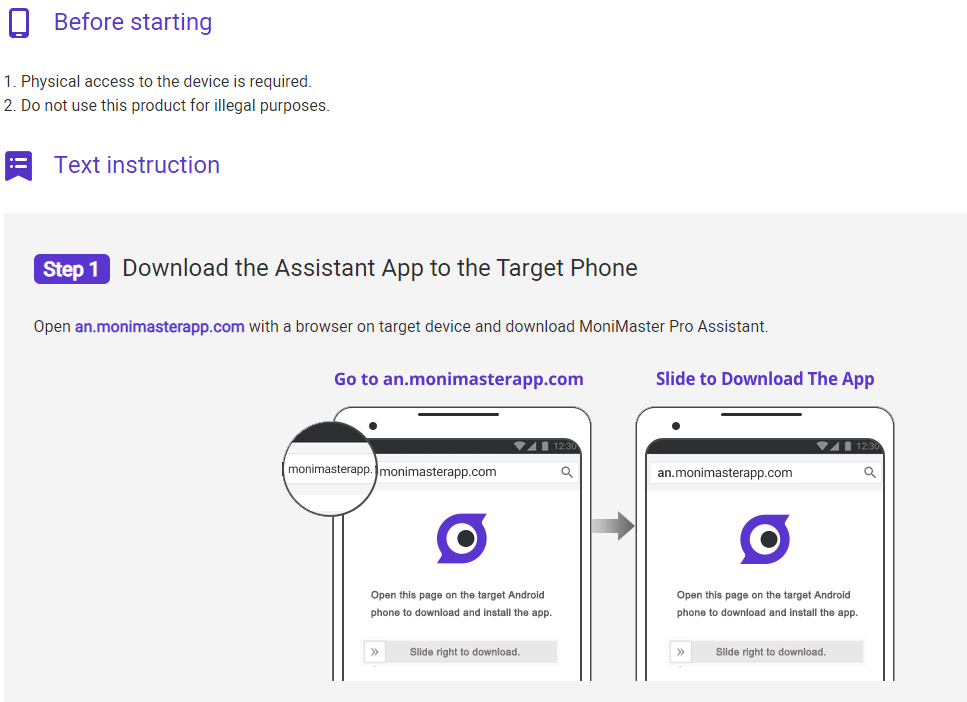
Step 3. Start Monitoring: The application is set to start monitoring. Start monitoring the target device on your browser.
With these 3 simple steps, you're on course for SIM card tracking or without tracking the target device.
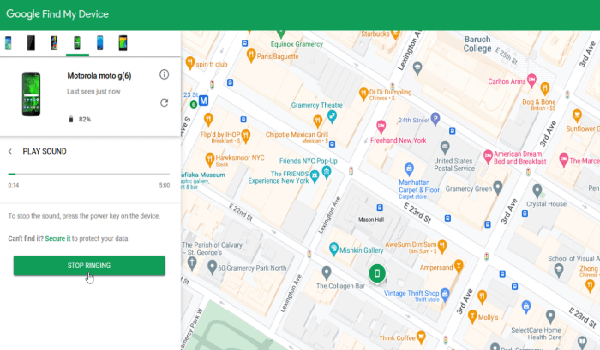
2Google Find My Device - For Android
You can find, secure, or erase your device remotely with Google Find My Device. The process is simple and easy. Find My Device automatically turns on if you have an added Google Account on your device. You can find, lock, or erase if it's connected to WiFi or mobile data.
You can track a phone without the SIM card in the following steps:
Step 1. Go to android.com/find.
Step 2. Sign in to your Google Account. Choose the stolen device from the sidebar if you have more than one device. For more than one user profile of the lost device, Sign in with a Google Account of the main profile.
Step 3. The lost device gets a notification.
Step 4. On the map, you'll get an approximate location that may not be correct. You may find the last location of the device if available for the list device.
Step 5. In case of a prompt, tap Enable lock & erase.
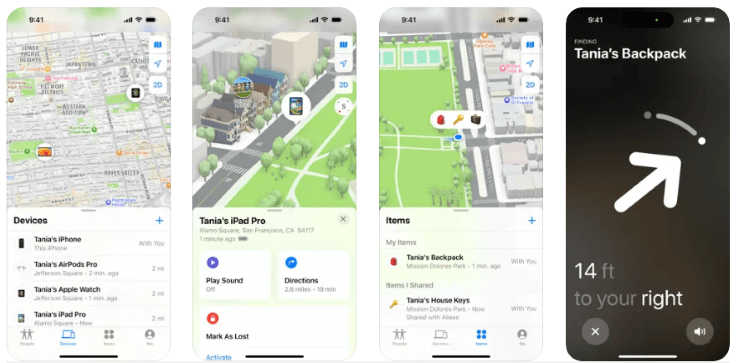
3My iPhone - For iPhone
Can a phone be tracked without a SIM? The Find My app for My iPhone and other Apple devices makes tracking a breeze. You can find your devices anywhere means you can leave them anywhere and track them easily. The process is simple and easy.
Step 1. Tap on a product icon. Some devices can send you the location within 24 hours even when turned off or with a low battery.
Step 2. You can play sound if the device is nearby. The latest AirPods cases have built-in speakers to deliver louder tones.
Step 3. Notify When Left Behind on your iPhone, you'll get a notification if the device is left at an unfamiliar location.
Step 4. Put in Lost Mode to track location. People can also reach you by simply viewing your message on the device's Lock Screen.
Step 5. Erase personal data and reset your iPhone if the device has fallen into the wrong hands. Retrieve data from iCloud backup as the iPhone is found.
AirTag Find My Technology or Precision Finding are also excellent sources to track your Apple devices.
4Track a Cell Phone via Google Maps
Can you track a phone without a SIM card with Google Maps? Yes, Google Maps is a credible source to track someone's cell phone location if the location services are enabled. You can do this in the following process:
Step 1. Many smartphones have also integrated Google Maps. You can install and launch the app.
Step 2. Sign in to your Google Account. For more than one device, select the lost device at the top of the sidebar. Sign in with a Google Account in case of more than one user profile.
Step 3. Enable Location Sharing. You can also choose how long you want the location to be on.
Step 4. Choose the contacts you want to share access to. You can share services by tapping the person's profile.
Step 5. Track the location of the device by sending a link to the targeted device through email or message. People can click on the link to locate your whereabouts.
Part 2. How to Find A Lost SIM Card Without Phone?
The above methods also work for finding a lost SIM card without a phone, but there are other methods that are not as effective as the above methods.
1Via Social Media Platform
In some cases, you can use platforms like Facebook Messenger, WhatsApp Web, or Instagram to check the last active status of your account. If you were logged in from a mobile device, the platform might show the last known location or activity status, which could hint at where the phone—and the SIM—was last active.
2Via IMEI Number
Every phone has a unique IMEI number. If you've recorded this number, you can report it to your mobile carrier or the police. Carriers can track the device when it connects to a network, even with a different SIM card. While the IMEI doesn't directly track the SIM, it can help recover the phone that contains it.
3Cell-tower triangulation (via carrier or law enforcement)
If your SIM is active and connects to the mobile network, your carrier or law enforcement (with the right permissions) can triangulate its approximate location using historical connection logs. StingRay (IMSI-catcher) devices can further narrow down location by pretending to be a cell tower.
4Use tag based tracking as a backup
If you anticipated loss, you might have placed a Bluetooth tracker (like Tile) on the device or case. While Bluetooth range is limited (~200 ft), networked crowdsourced tracking may help if someone with the tracker app passes nearby.
For future SIM safety, consider pre-installing a SIM tracking app or keeping a small GPS tracker with your SIM.
If already lost, contact your carrier—ask if they can trace tower connections or block the SIM to prevent misuse.
Check for found item services (e.g., local police station, transit lost & found) often overlooked.
Part 3: FAQs about Can a Phone be Tracked without a SIM Card
1 Can you track a phone that has a SIM card inserted but no service?
Yes, you can track a phone without service. Install a unique tracking app such as MoniMaster. It creates a device ID if the device is set up and never changes that you can use to track the device remotely.
2 Is it possible to track a phone's location using Wi-Fi without a SIM Card?
Yes, tracking a phone using WiFi without a SIM card is extremely easy these days. Sign in to your Google Account, enable location services, and connect to the internet. Visit Android's tracking website. You may find your device if you are lucky enough.
3 Can you track a phone if it's been factory reset?
If the factory is reset, the possibility of tracking your device is limited. Tracking a phone is nearly impossible without a working internet connection. However, you can locate a device with some methods. For instance, use a Google Home Speaker and link it to your Google account. It allows you to find the phone if it's in silent mode by ringing the alarm. However, it is only workable at a certain distance. The next method is tracking with an IMEI number as it is unique on each phone.
4 Can IMEI number be tracked without SIM?
Yes, an IMEI number can be tracked without a SIM card. Here are some ways this can be done:
- IMEI Tracking: The IMEI number can be used to track a device through cell towers even if there is no SIM card present, as long as the device is turned on.
- WiFi and Location Services: Phones can also be tracked using WiFi and location services. By signing into your Google Account or using similar services, you can enable location tracking without a SIM card.
5 How to find lost SIM Card without phone?
Finding a lost SIM card without a phone is challenging, but here are some steps that might help:
- Contact Your Service Provider: Reach out to your mobile service provider. They may be able to assist with locating or deactivating the SIM card to prevent misuse.
- File a Police Report: If you believe the SIM card was stolen, file a police report. This may not directly help in finding the SIM card, but it could be necessary for security and to prevent unauthorized use.
- Track via Cell Network: If the SIM card is inserted into a phone, it can be tracked through the network using the IMEI number of the phone.
Part 4: Summary
Several phone company-oriented, third-party apps and other sources are available to track the location of the phone. Sources can also help track plan members, plan travel routes, and monitor employees. We highly recommend MoniMaster to ensure optimum level tracking. Location tracking of the phone without a SIM card is a breeze with this excellently built application!

















